Exploring crucial terminal emulation capabilities
CIO
OCTOBER 16, 2023
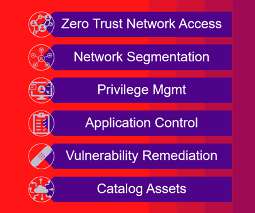
Features such as encryption protocols, secure authentication mechanisms, and secure data transmission help safeguard confidential information during remote sessions. Advanced security features provide peace of mind and help organizations meet compliance requirements in various industries. Protocols can include certified TLS 1.3



















































Let's personalize your content