Cybersecurity Snapshot: Log4j Anniversary, CI/CD Risks, Infostealers, Email Attacks, OT Security
Tenable
DECEMBER 9, 2022
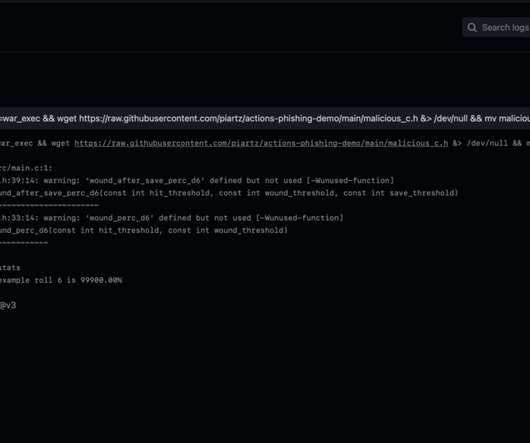
It was at around this time last year that the discovery of the zero-day Log4Shell vulnerability in the ubiquitous Log4j open source component sent shockwaves through the worlds of IT and cybersecurity. . 2 - OWASP’s top 10 CI/CD security risks. Inadequate Identity and Access Management. Dependency Chain Abuse.















































Let's personalize your content