A CIEM Leader and Outperformer
Prisma Clud
MARCH 20, 2024
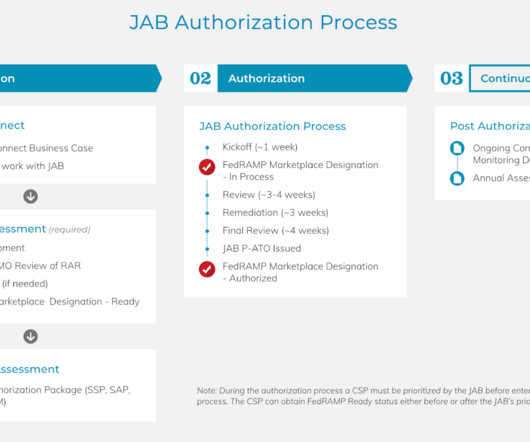
Identity and access management (IAM) in the cloud is challenging. The CIEM Market is Evolving CIEM as a category is relatively new, first appearing in 2020 to address the new challenges of managing identities in the cloud. Especially as organizations deal with entitlement sprawl and managing machine identities.

















































Let's personalize your content