Tap Into Your Inner Logs for Better Anomaly Detection and Incident Response
Tenable
JANUARY 19, 2024
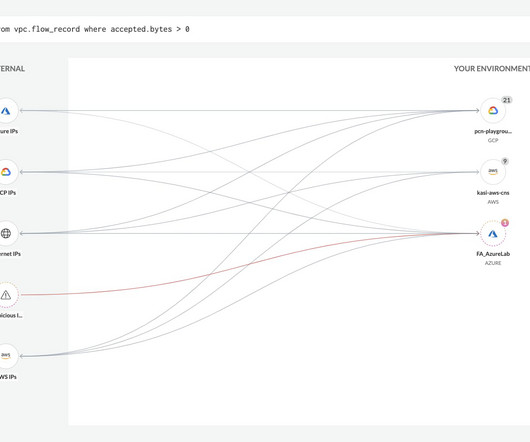
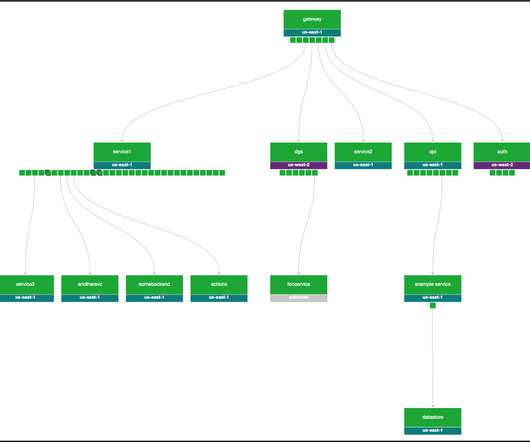
Tenable Cloud Security enriches cloud activity log data to give you the context you need to quickly respond to and remediate cloud risks. With so many tools at their disposal, you might wonder why security teams continue to struggle with detection and response times. The average total cost of a data breach increased 2.8% in 2023 to $4.45














































Let's personalize your content