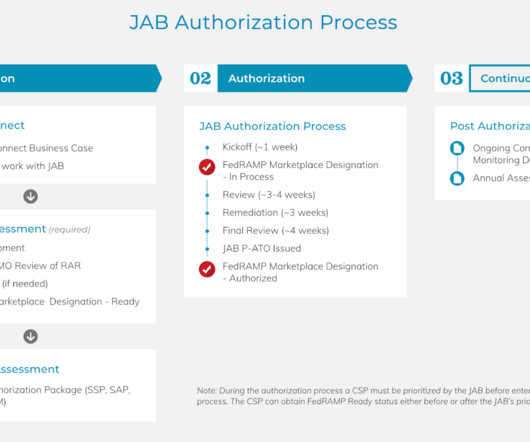
Host Intrusion Detection for Compliance in AWS and Multicloud Environments
Lacework
JUNE 5, 2019
These are not a one-size-fits-all type of occurrence, either; they happen at the application, ID, workload, and host layers of the cloud. The post Host Intrusion Detection for Compliance in AWS and Multicloud Environments appeared first on Lacework.





















































Let's personalize your content