How security fears are driving network modernization
CIO
DECEMBER 8, 2022
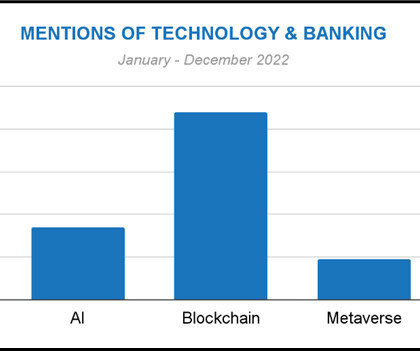
NTT’s research finds that two in three organizations confirm their technical debt has accumulated, with 71% saying that low network maturity levels are negatively impacting their operational delivery and ability to meet business goals. For example, 79% told researchers their security strategy is fully aligned with business strategy.




















































Let's personalize your content