ipconfig vs ifconfig – Difference between ipconfig and ifconfig
The Crazy Programmer
MAY 21, 2021
In this article, we will have a look at the two network configurations in computer networks – ipconfig and ifconfig. Network configuration is the process of assigning and arranging the network controls in a manner to perform specific tasks. Ipconfig stands for Internet Protocol configuration. What is ipconfig?

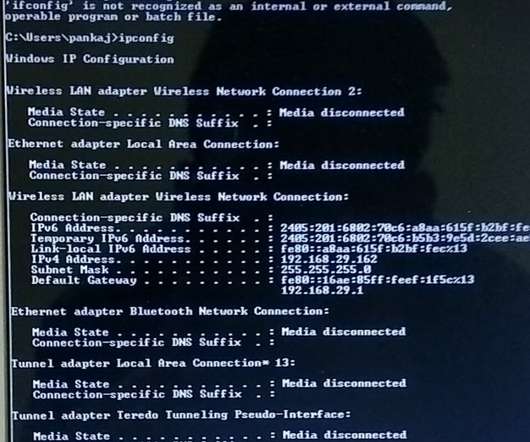













































Let's personalize your content