How ML System Design helps us to make better ML products
Xebia
AUGUST 9, 2023
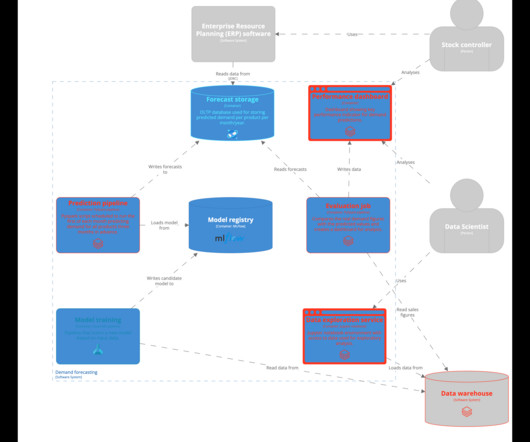
With the industry moving towards end-to-end ML teams to enable them to implement MLOPs practices, it is paramount to look past the model and view the entire system around your machine learning model. The classic article on Hidden Technical Debt in Machine Learning Systems explains how small the model is compared to the system it operates in.


















































Let's personalize your content