Why CIOs back API governance to avoid tech sprawl
CIO
FEBRUARY 7, 2024
Most companies have transitioned to become more software-centric, and with this transformation, application programming interfaces (APIs) have proliferated. But APIs do more than support next-generation technologies — they already serve a foundational purpose within most enterprises.



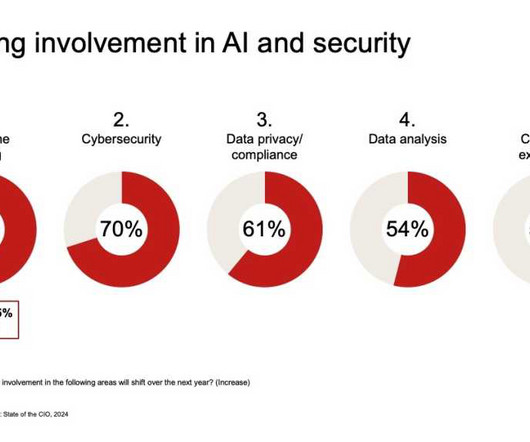















































Let's personalize your content