Metadata Management and Data Governance with Cloudera SDX
Cloudera
JANUARY 26, 2024
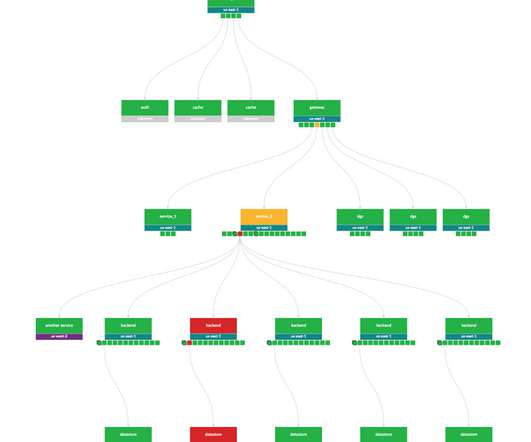
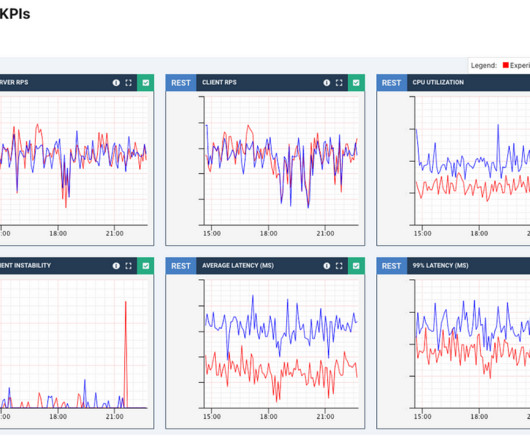
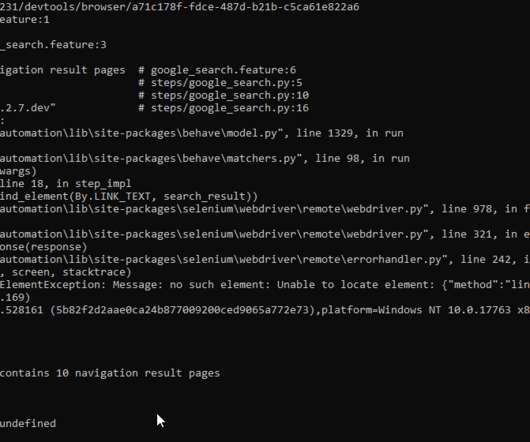
This will allow a data office to implement access policies over metadata management assets like tags or classifications, business glossaries, and data catalog entities, laying the foundation for comprehensive data access control. View and access entities that are classified with tags related to “finance.”












































Let's personalize your content