Towards Efficient Labeling in Federated Learning
Dataiku
JANUARY 6, 2023
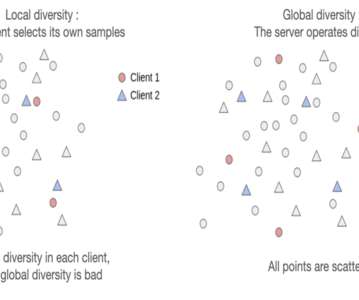
Federated Learning (FL) can enable privacy-preserving distributed computation across several clients. It is used to federate knowledge from parties that do not wish to share their data.


















































Let's personalize your content