Just Released and Ready for Download — Software Firewalls for Dummies
Palo Alto Networks
SEPTEMBER 19, 2023
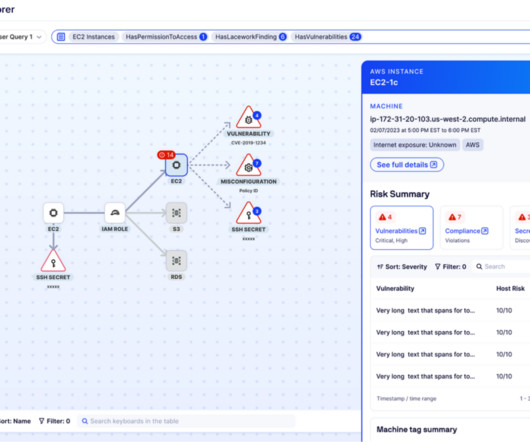
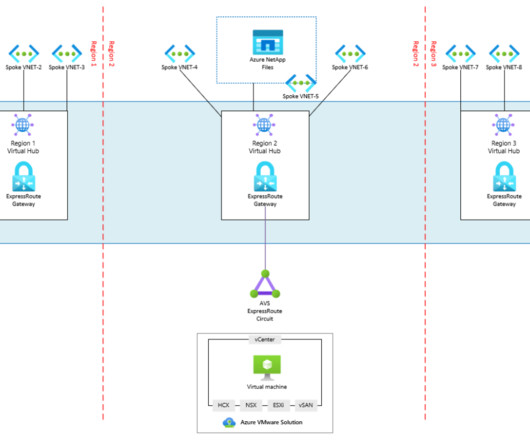
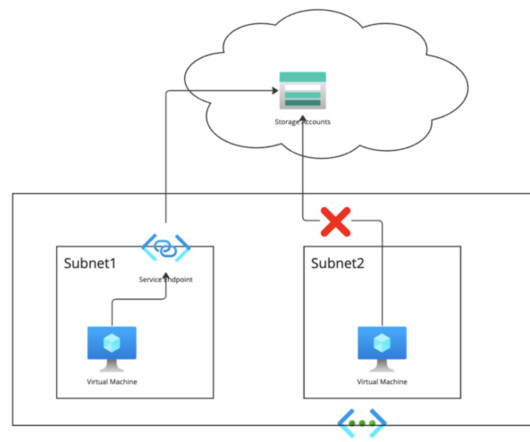
If you want to protect applications and workloads throughout today’s complex and interrelated environments, you need software firewalls. You can better understand the extensive need and numerous use cases for virtual firewalls, container firewalls and managed cloud firewalls with our essential guide, “ Software Firewalls for Dummies.”
















































Let's personalize your content