Top 5 Organization Policy Services for Google Cloud
Xebia
JUNE 27, 2023
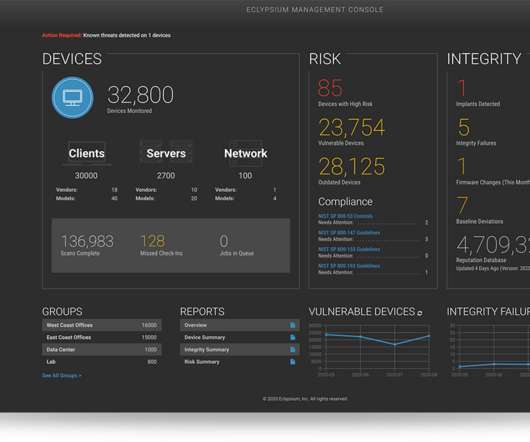
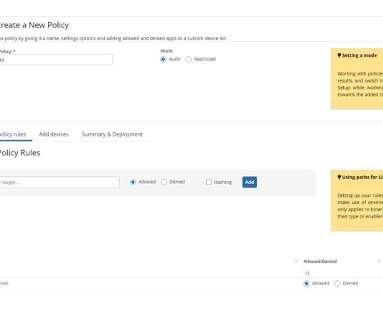
Top 5 Organization Policy Services for Google Cloud The Google Cloud is a cloud service that enables users to create and manage virtual machines and Kubernetes clusters, store data, and run applications. When using Google Cloud, it’s important to implement technical boundaries that enforce your company’s security and privacy policies.



















































Let's personalize your content