Why Internet Performance Monitoring is the new frontier in a distributed world
CIO
MARCH 25, 2024
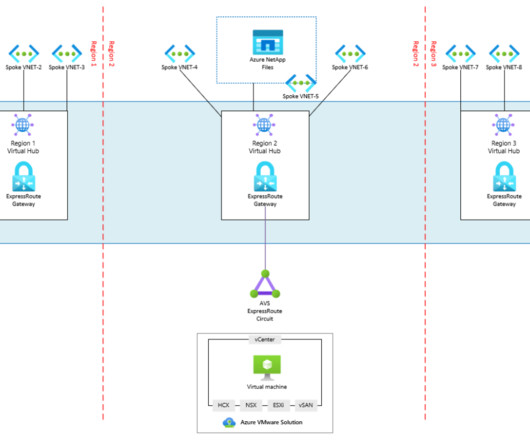
This ecosystem relies heavily on core internet services such as DNS and BGP, while networks have evolved to embrace a variety of complex architectures, including IPv4/6, WAN, SD-WAN, SASE, EDGE, and 5G technologies. Learn more about how to ensure the resilience of your Internet Stack with IPM Networking














































Let's personalize your content