Why Are Video Devices Becoming More Popular?
Strategy Driven
JANUARY 12, 2024
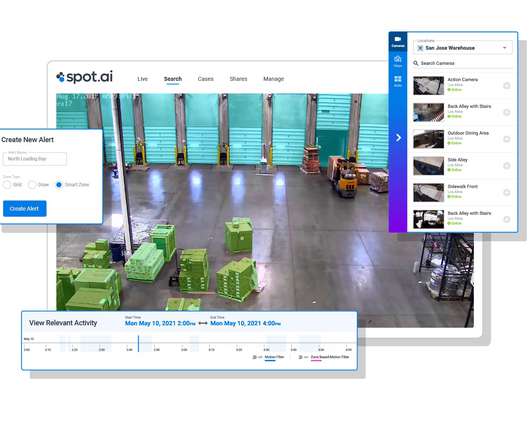
Video is transforming business-to-business (B2B) and business-to-customer (B2C) communications. The critical technologies making this possible are lowering latency and enabling remote access to video content. Video Phones Video phones, also called videoconferencing devices, allow two people to communicate by video and audio.




















































Let's personalize your content