Deploying a Sitecore instance on a “local” Kubernetes (k8s) setup
Perficient
FEBRUARY 14, 2023
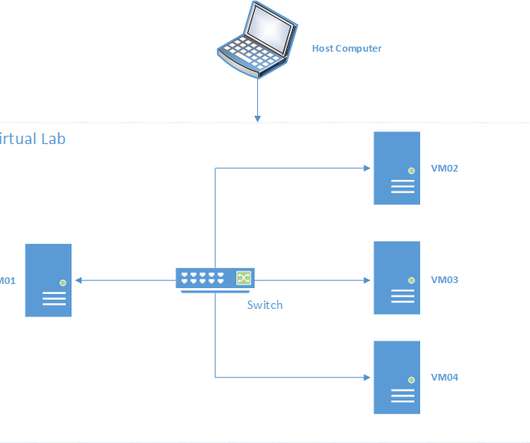
In this blog series I will be sharing the details my journey, my findings the mistakes/successes, and the final state of my discovery. The Research So my research took me to various tools, from Minikube , Kind to the recently released AKS Edge Essentials Preview from Microsoft TechCommunity.



















































Let's personalize your content