How to minimize remote access cyber security threats in 2024
CIO
JANUARY 22, 2024
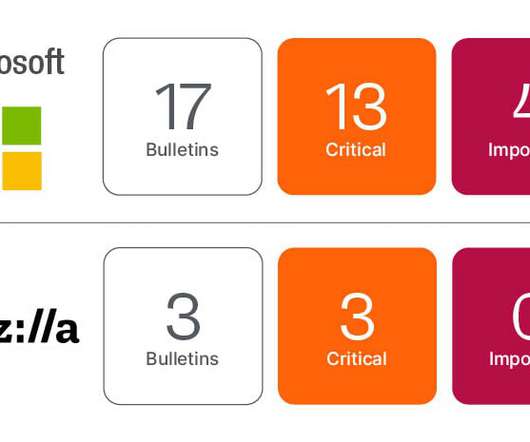
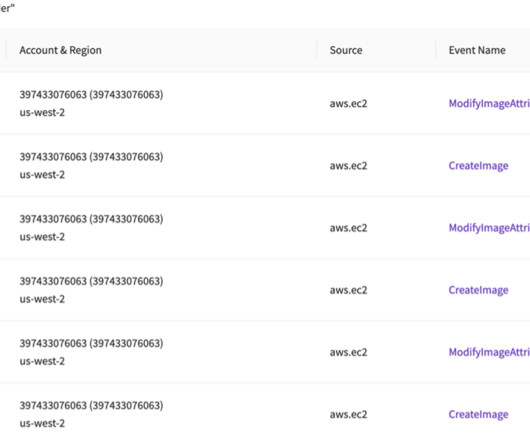
Cloud is the dominant attack surface through which these critical exposures are accessed, due to its operational efficiency and pervasiveness across industries. Over 85% of organizations analyzed have RDPs accessible via the internet for at least 25% of a given month, leaving them open to ransomware attacks.
















































Let's personalize your content