The AI cat and mouse game has begun
CIO
APRIL 29, 2024
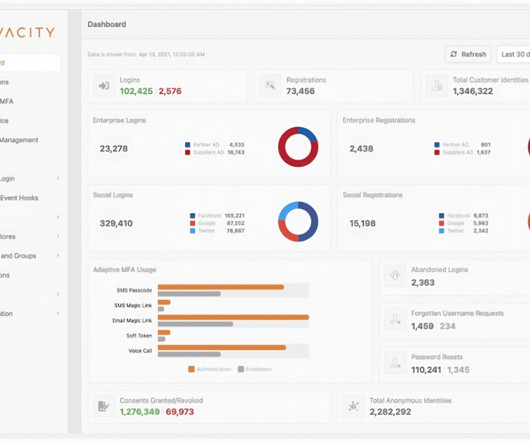
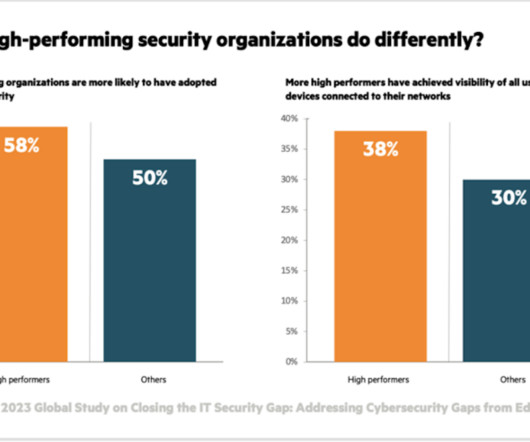
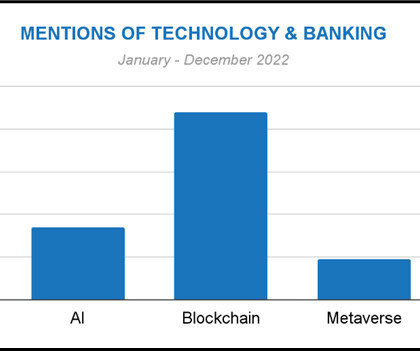
Cutting-edge solutions are available that utilize AI for detecting and validating identities and authorizing transactions in real time, offering a potent countermeasure against these sophisticated attacks. AI-based identity management and access control technologies are essential for enhancing cybersecurity measures.


















































Let's personalize your content