AI, cybersecurity investments and identity take center stage at RSA 2024
CIO
MAY 29, 2024
It was truly a good use of time attending the 33rd RSA Conference in San Francisco, along with over 40,000 attendees, networking with the leading minds in the cybersecurity industry. Above all, there was a palpable focus on what it will take to make organizations combat-ready for the next waves of cybercrime and how best to manage it all.



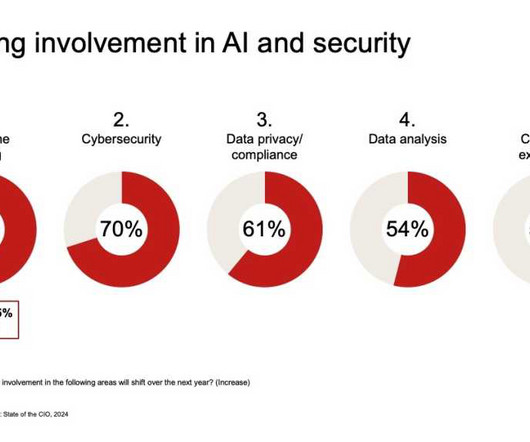



































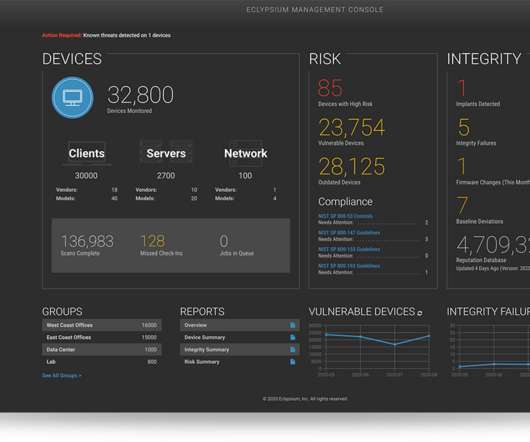











Let's personalize your content