Cybersecurity Solutions Your Business Must Have
Kaseya
MAY 11, 2020
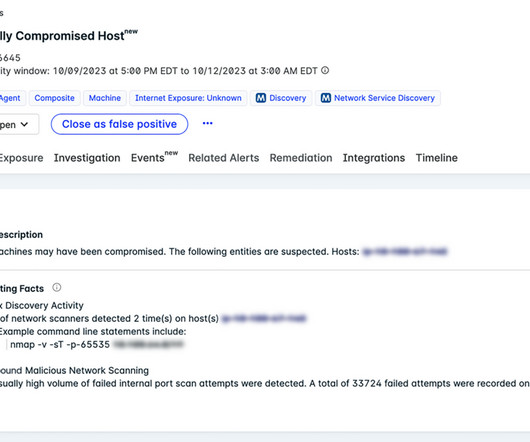
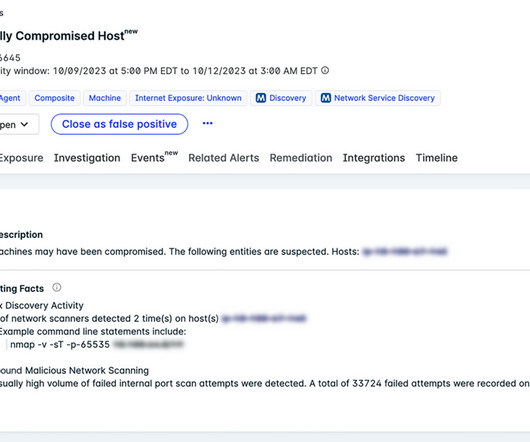
In this blog, we’ll take a broader look at cybersecurity solutions in three key areas that can help you build a solid foundation for overall IT security. Endpoint Security. Endpoint security is the process of protecting individual devices with the broader aim of securing the network and the data of the organization.











































Let's personalize your content