Driving 15 years of IT transformation in 5
CIO
MARCH 21, 2024
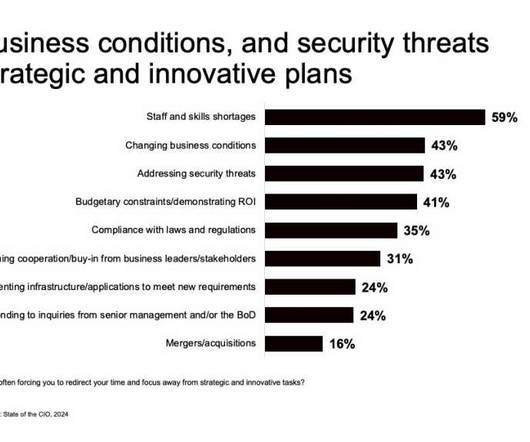
To address the growing pains, Lovelady reinforced the importance of strategic planning for IT. These include network management, help desk, establishing and enforcing policies related to information security and risk management, and several other IT functions. The company, after all, had been successful historically.




















































Let's personalize your content