Threat Hunting to Find the Good Stuff
Palo Alto Networks
OCTOBER 17, 2023
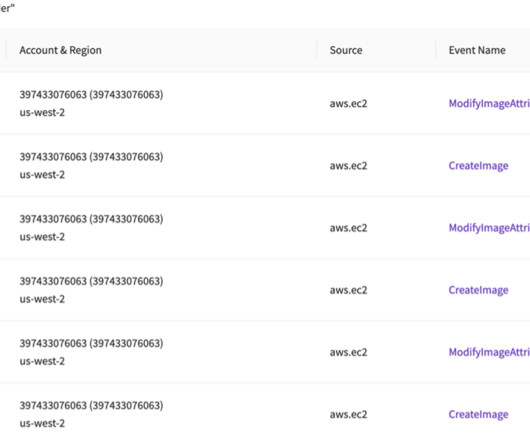
In the final episode of Season One of “This is How We Do It,” Peter Havens from Cortex product marketing sits down with Leeroy Perera, staff security engineer. They discuss the practice of threat hunting and how we apply it in our SOC. To combat this threat, Leeroy emphasizes the significance of threat hunting.





















































Let's personalize your content