The Basics of Configuration Compliance
Lacework
FEBRUARY 27, 2023
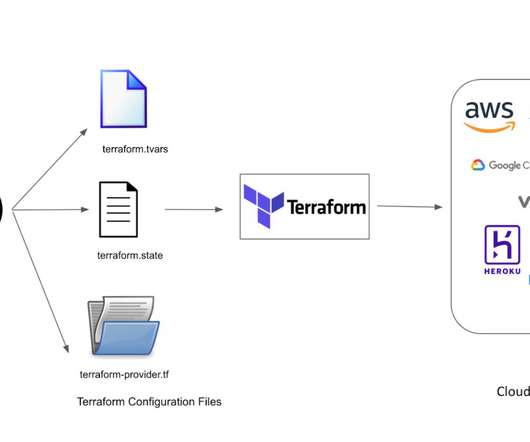
The public cloud has enabled customers to move fast and adapt to changing needs by allowing them to quickly spin up infrastructure programmatically or with just a few clicks. This has allowed companies to grow quickly, and for technological advancements to be implemented rapidly.















































Let's personalize your content