5 C-suite bridges every IT leader must build
CIO
MAY 22, 2023
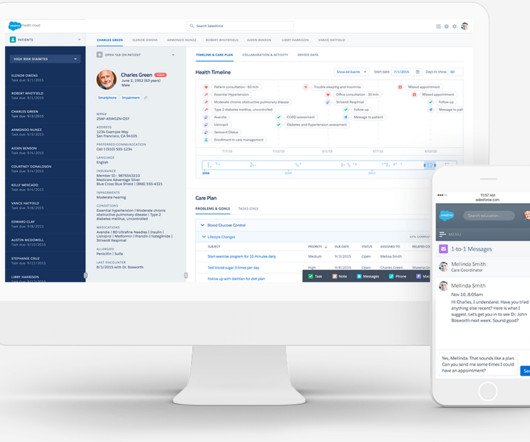
A recent Gartner survey found that 41% of employees outside IT are “business technologists” who spend at least part of their time working on technology. Chief financial officer In a recent survey by financial software company Coupa, 33% of CFOs said they felt more tension with CIOs than with any other leader at their company.








































Let's personalize your content