Primer: The next act for security theater
The Parallax
AUGUST 23, 2018
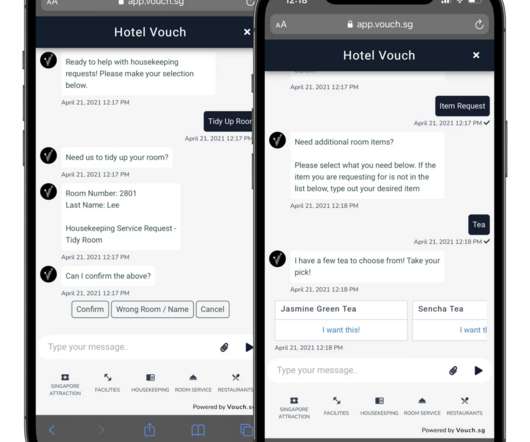
The day after DefCon concluded this year, a prominent cybersecurity researcher and hacker known as the brain behind hacks featured on hit TV show Mr. Robot offered his resignation as the head of its security operations. Why are Androids less secure than iPhones? We MUST NOT let our hotels become like our airports.

















































Let's personalize your content