Bastion is an all-in-one cybersecurity solution for small businesses
TechCrunch
APRIL 26, 2023
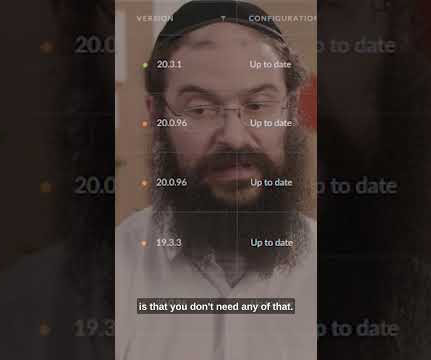
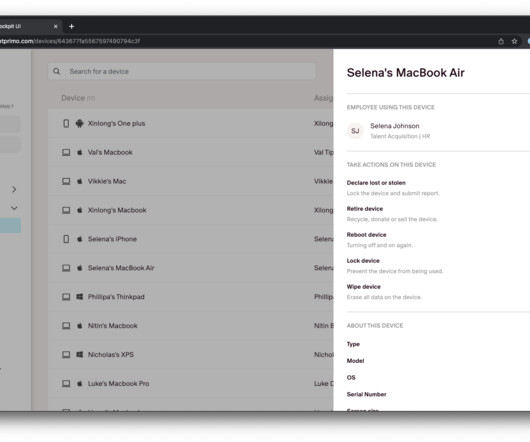
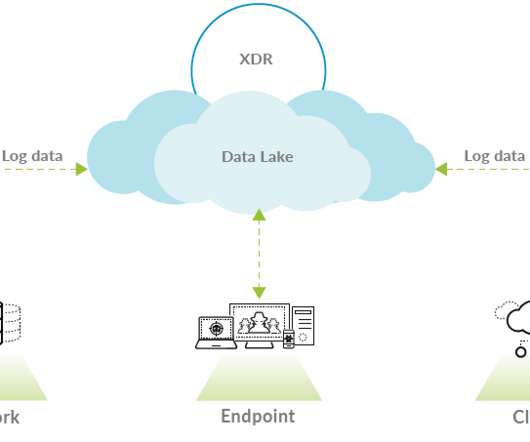
It bundles several different products that all revolve around cybersecurity risks with a software-as-a-service approach. Companies we talk with tell us: ‘We have an insurance broker, an accountant, why would we have multiple cybersecurity products?’” EDR stands for ‘endpoint detection and response’.
















































Let's personalize your content