Optimizing VoIP: Good Use Case for Enterprise Metrics And Monitoring
CTOvision
JANUARY 24, 2014
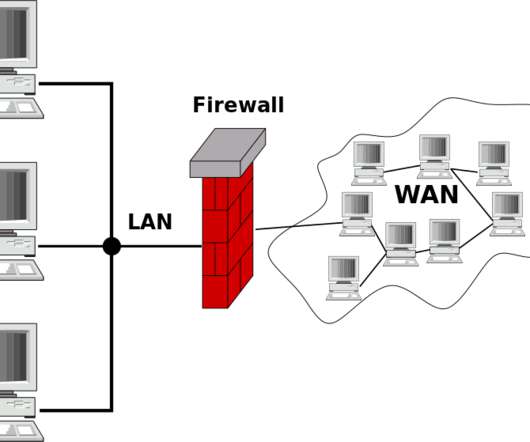
Voice over IP (VoIP) is one of the most widely deployed enterprise IT capabilities, and it is also one of the greatest contributions to business success IT provides. VoIP also comes with its own unique issues. VoIP uses IP so there are many avenues that must be continually considered when it comes to mitigating these attacks.










































Let's personalize your content