IT staff shortages damage the bottom line: IDC report
CIO
MAY 15, 2024
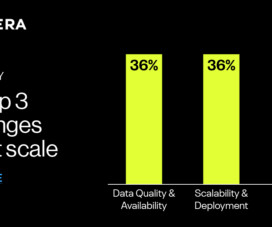
Nearly two thirds of the IT executives surveyed said “a lack of skills has resulted in missed revenue growth objectives, quality problems, and a decline in customer satisfaction. But it does require specialized training. But many enterprises’ training efforts are falling short. A new IDC report delivers those details.





















































Let's personalize your content