2F Authentication with Google Authenticator in Spring Boot
InnovationM
JULY 6, 2023
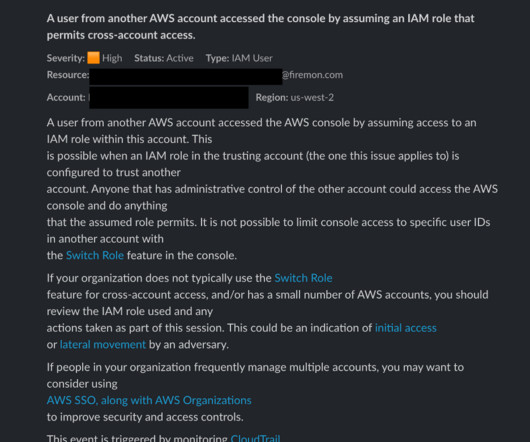
In today’s digital world, security is a major concern, and 2-factor authentication (2FA) is one way to increase security. 2FA adds an extra layer of protection to your account by requiring users to provide two forms of authentication to access it.


















































Let's personalize your content