How to create and update Google terraform provider magic modules resource definitions
Xebia
DECEMBER 31, 2023
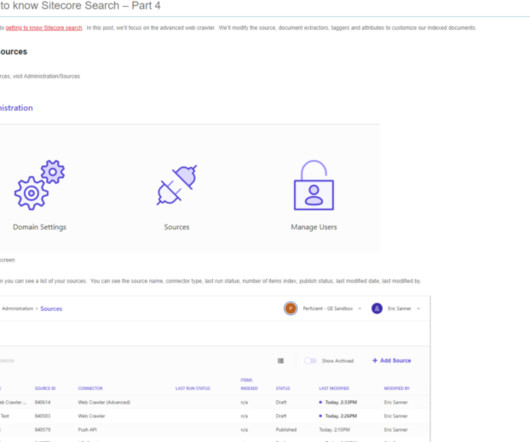
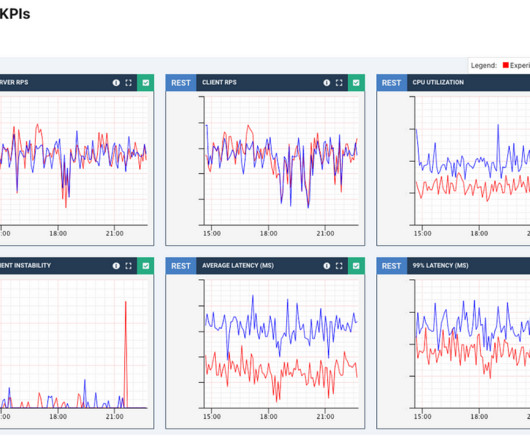
In this blog I will show you how you can quickly generate and update these resource definitions using a simple utility. I wanted to write a blog about it, and showcase the configuration with terraform templates. ruby/object:Api::Type::Integer WARNING: mismatch of type on field Service.template.labels, existing tag !ruby/object:Api::Type::KeyValuePairs















































Let's personalize your content