Enhancing Transportation Cybersecurity and Fleet Management for the DoD
Tenable
MARCH 25, 2024
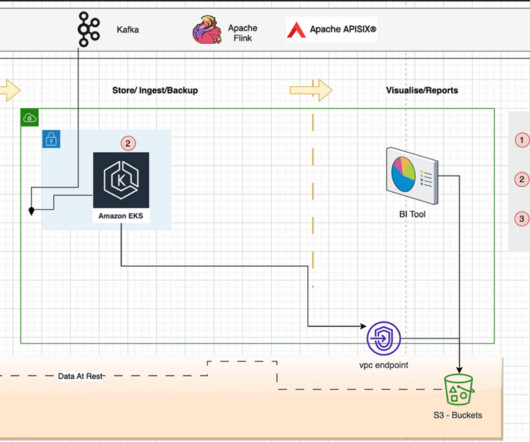
However, fleet management in the modern age comes with its own set of challenges. In this blog post, we’ll outline the challenges involved in protecting the DoD’s transportation systems from cyberattacks, and offer OT security recommendations.



















































Let's personalize your content