How Zero Trust is supposed to look
CIO
DECEMBER 19, 2023
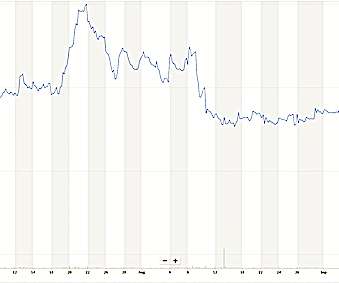
Zero trust for users Your users need fast, secure, and reliable access to applications and the internet from anywhere and everywhere. virtual machine, container, microservice, application, storage, or cloud resource) used either as needed or in an always-on fashion to complete a specific task; for example, AWS S3.













































Let's personalize your content