Building Resilient Public Networking on AWS: Part 1
Xebia
NOVEMBER 28, 2023
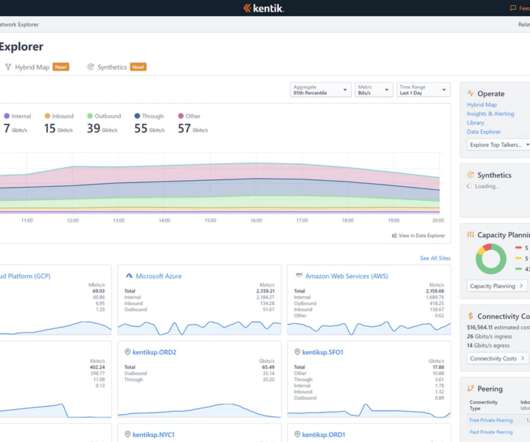
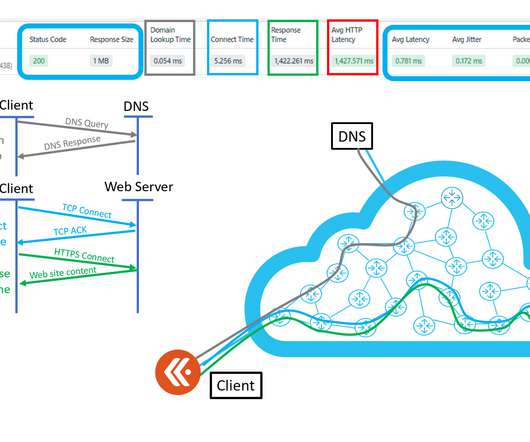
Revisiting Networking Concepts from the Client’s Perspective Welcome to our comprehensive blog series on advanced networking strategies tailored for regional evacuation, failover, and robust disaster recovery. So, buckle up and join us on this exhilarating journey to uncover the secrets of resilient networking on AWS.


















































Let's personalize your content