Credential Stuffing Attacks – Definition, Detection and Prevention
The Crazy Programmer
MARCH 25, 2021
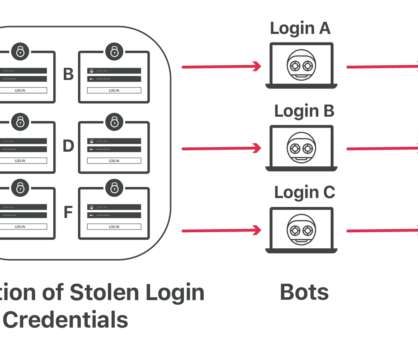
Look for any attempts to remove credential-based login and to replace it with password-less authentication. Use the following tips to keep attackers away from using credential stuffing attack on your business: Multi-Factor Authentication. Most of them cannot even work with multiple authentications. API Security.




















































Let's personalize your content