TransUnion transforms its business model with IT
CIO
APRIL 26, 2024
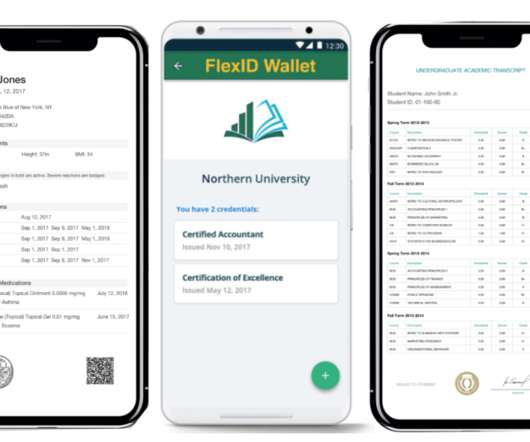
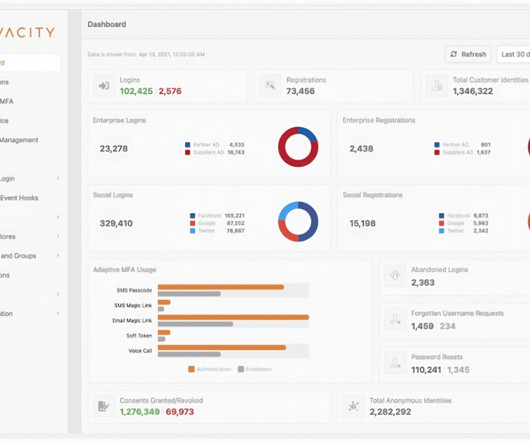
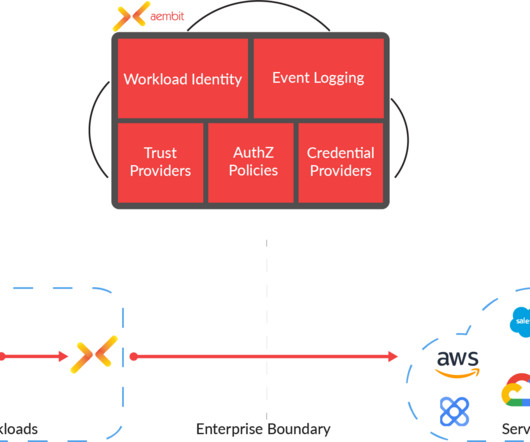
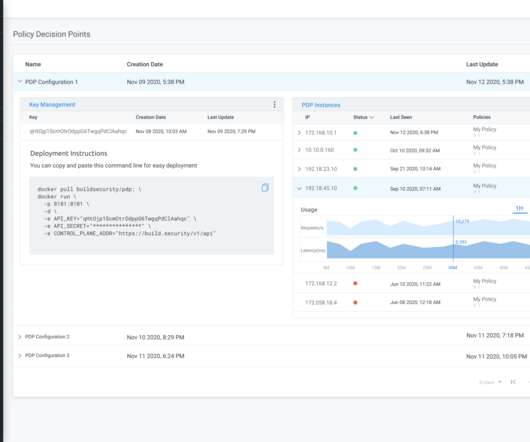
Count TransUnion among the rising tide of enterprises evolving their identities thanks to IT. “We That data is in the process of being unified on a multilayered platform that offers a variety of data services, including data ingestion, data management, data governance, and data security.



















































Let's personalize your content