What is COBIT? A framework for alignment and governance
CIO
JUNE 12, 2023
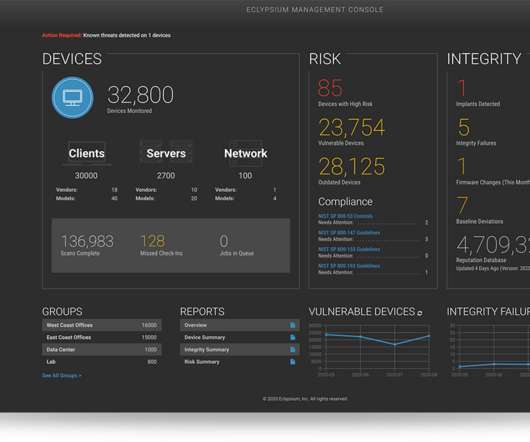
COBIT is an IT management framework developed by the ISACA to help businesses develop, organize, and implement strategies around information management and IT governance. Later, in the 2000s, the ISACA developed version 3, which brought in the IT management and information governance techniques found in the framework today.















































Let's personalize your content