Eclypsium lands $25M to secure the device supply chain
TechCrunch
OCTOBER 4, 2022
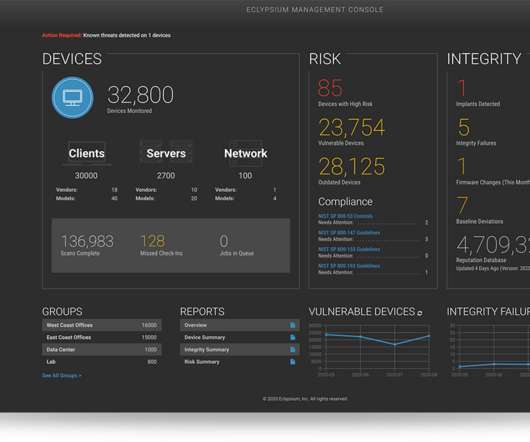
As the enterprise device supply chain grows increasingly global and fragmented, it’s becoming more challenging for organizations to secure their hardware and software from suppliers. Eclypsium’s cloud management dashboard Image Credits: Eclypsium.


















































Let's personalize your content