Is Your Internet Connection Damaging Your Business?
Megaport
JULY 5, 2022
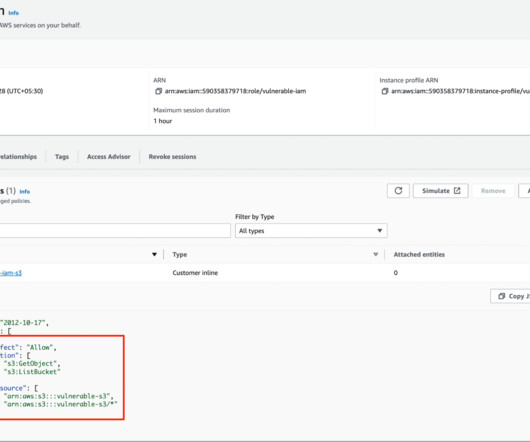
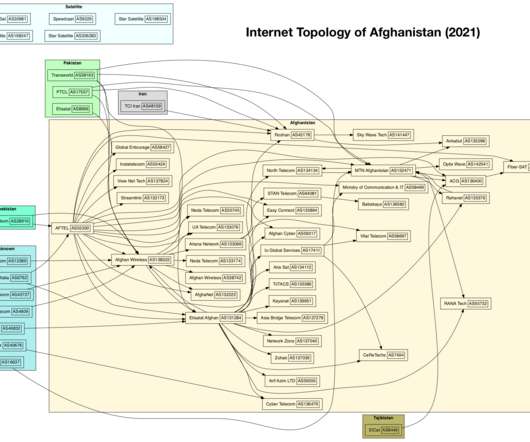
Cloud-based services are essential for many businesses, offering employees a virtual office and the flexibility to connect from anywhere, at any time. Public cloud networks and.




















































Let's personalize your content