CIOs eager to scale AI despite difficulty demonstrating ROI, survey finds
CIO
APRIL 25, 2024
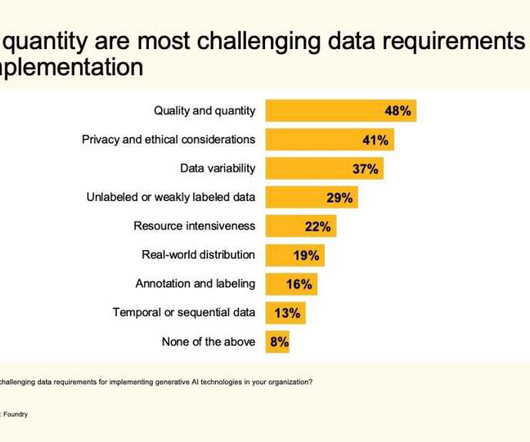
CIOs rank AI as a top priority alongside cybersecurity for IT departments. However, barriers such as adoption speed and security concerns hinder rapid AI integration, according to a new survey. There is a sense of urgency to leverage AI effectively, but adoption speed and security challenges are hindering efforts.


















































Let's personalize your content