Fix a faulty Virtual Machine Using Nested Virtualization in Azure
Cloud That
NOVEMBER 28, 2022
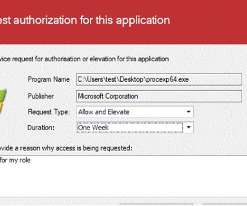
Step-by-Step Guide for troubleshooting faulty Virtual Machines and the Creation of Rescue Virtual Machines. You can design your virtualization environments using nested virtualization, which permits you to run virtual machine (VM) instances inside other VMs. Review and create the VM after validation is successful.


















































Let's personalize your content