Radically simplify and expand Zero Trust to cloud workload
CIO
DECEMBER 21, 2023
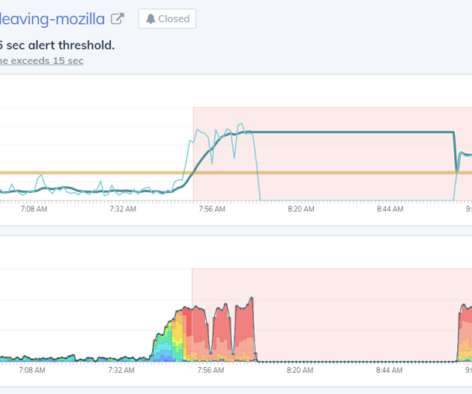
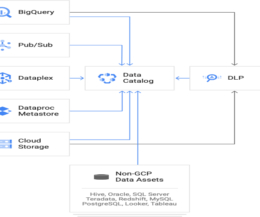
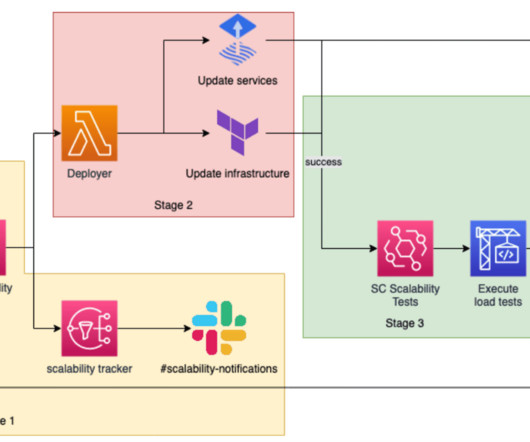
With an ever-evolving threat landscape that capitalizes on an expanding attack surface, we’re seeing a substantial rise in the number of security breaches and threats that negatively impact businesses. Protecting these complex environments and connectivity with the right approach has become a necessity.















































Let's personalize your content