How security fears are driving network modernization
CIO
DECEMBER 8, 2022
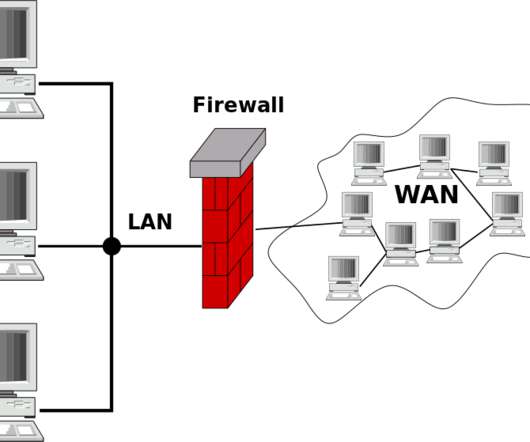
The shift to hybrid working requires more openings in firewalls, which in turn places a premium on frequent upgrades to firewall protections. Research findings show that 93% of organization see the convergence of security and networking as a key focus of how future network characteristics will be changing.


















































Let's personalize your content