Bitwarden acquires Passwordless.dev to help companies authenticate users without passwords
TechCrunch
JANUARY 18, 2023
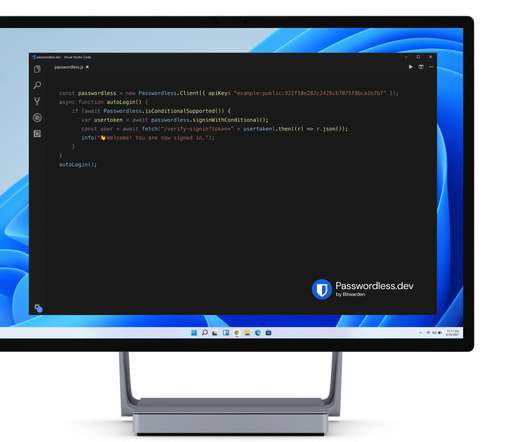
Open source password management platform Bitwarden has made its first known acquisition, snapping up a fledgling Sweden-based startup called Passwordless.dev , which specializes in helping developers integrate passwordless authentication technology into their software. Image Credits: Passwordless.dev. .

















































Let's personalize your content